![[TRex documentation]](../media/logo.gif)
![[TRex documentation]](../media/logo.gif)
|
TRex version 2.1.2User's Guide - Secure Deployment |
This documents talks about this last part and, basically, how to deploy TRex safely.
So, all the connections from and through TRex/web server, as shown in red in the next figure, should be securized (the blue ones are TRex responsibility).
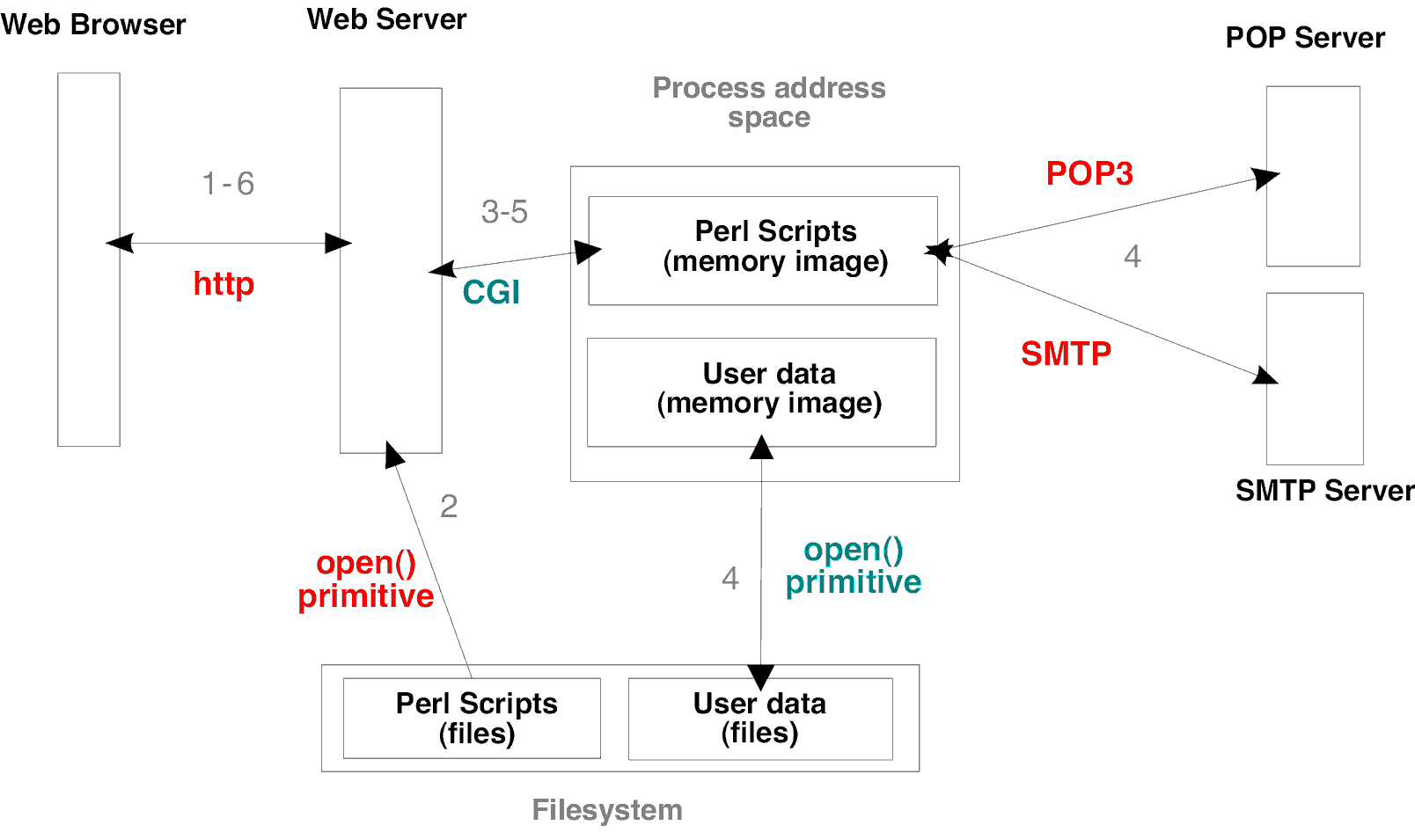
If you are using a web server in your machine there's nothing to worry about, beacuse the communication between your browser and web server is internal to the machine. Otherwise, if you plan to use it hosted in a web server other than your own local machine, take the precautions to encrypt the data exchange: use http over SSL (Secure Socket Layer) or TLS (Transport Layer Security - RFC 2246).
Because there's a lot of implementation for each component (web server, certificates, web browsers, etc.) we will give only generic directions about how to implement it, but for more specific instructions you will be redirected to the proper sites.
Basically https (http+SSL or http+TLS) encrypts the information using symetric algorithms (the same password is used to convert the plaintext in an encrypted form and to recover the plaintext), whose password is exchanged using an asymetric algorithm (one password is used to encrypt and the other one to decrypt). The password for the symetric algorithm is generated at random, but for the asymetric one relay on the use of certificates: the browser has some of them pre-installed and in the web server side a new certificate must be generated and installed.
As a general rule you will run the web server as a certain user (let's say http_user), then give the minimum permissions to that user that allows the proper TRex operation (don't let it to logon interactively, don't give it administrative permissions, etc.). In the next section there's a few lines about http_user filesystem permissions.
For using https in some web servers, the next links can be used for information :
Apache download: http://httpd.apache.org/dist/
Apache manual (install, setup, use, ...): http://httpd.apache.org/docs/
Apache crypto module download: http://www.modssl.org/source/
Apache crypto module (install, setup, use, ...) : http://www.modssl.org/docs/
Apache certificate install: http://www.verisign.com/support/tlc/csr/modssl/v00.html
ApacheSSL download: http://www.openssl.org/source/
ApacheSSL manual (install, setup, use, ...): http://www.openssl.org/docs/
ApacheSSL certificate install: http://www.verisign.com/support/tlc/csr/ssleay/v01.html
iPlanet Fasttrack: http://www.iplanet.com/products/infrastructure/web_servers/fast_trck41/index.html
iPlanet download: http://www.iplanet.com/downloads/download/index.html
iPlanet docs: http://docs.iplanet.com/docs/manuals/enterprise.html
iPlanet certificate install: http://www.verisign.com/support/tlc/class3_install_docs/netscape/v04e.html (the link if for Enterprise server, but it should work pretty similar)
MS IIS download: http://www.microsoft.com/downloads
MS IIS info page: http://www.microsoft.com/windows2000/guide/server/features/web.asp
MS IIS certificate install: http://www.verisign.com/mcsp/IIS_Tech.pdf
MS IIS & SSL troubleshooting: http://www.verisign.com/support/tlc/commercesite/tsiis.html
There's not too much to say about this, just that the scripts (the path specified by TRex::Common:$script_path) should be given read and execute permission for the http_user, and read and write permissions at the data files (the path specified by TRex::Common:$db_path).
![[TRex documentation]](../media/logo.gif)
|
TRex version 2.1.2User's Guide - Secure Deployment |